Bad Passwords
Ibrahim Uruc Tarim
About the Dataset
Useful Variables
- Password: The actual password string.
- Category: This column categorizes passwords, based on their complexity or style (e.g., ‘password-related’, ‘simple-alphanumeric’ or relation).
- Value and Time Unit: These two columns appear to relate to the strength or vulnerability of the password, possibly indicating how long it would take to crack the password. ‘Value’ gives a numerical figure, and ‘time_unit’ provides the unit of time (e.g., years, minutes, seconds).
- Offline Crack Sec: This might indicate the time in seconds it would take to crack the password using offline methods.
- Strength: A numerical representation of the password’s strength.
Unveiling Password Vulnerabilities
Predictable Patterns: Common Password Categories
- Top Trends: Names and simple patterns lead as the most common choices.
- Preference for Easy: Users tend to prefer memorable over complex passwords.
- Vulnerability by Category: Popularity in these categories often equates to higher risk.
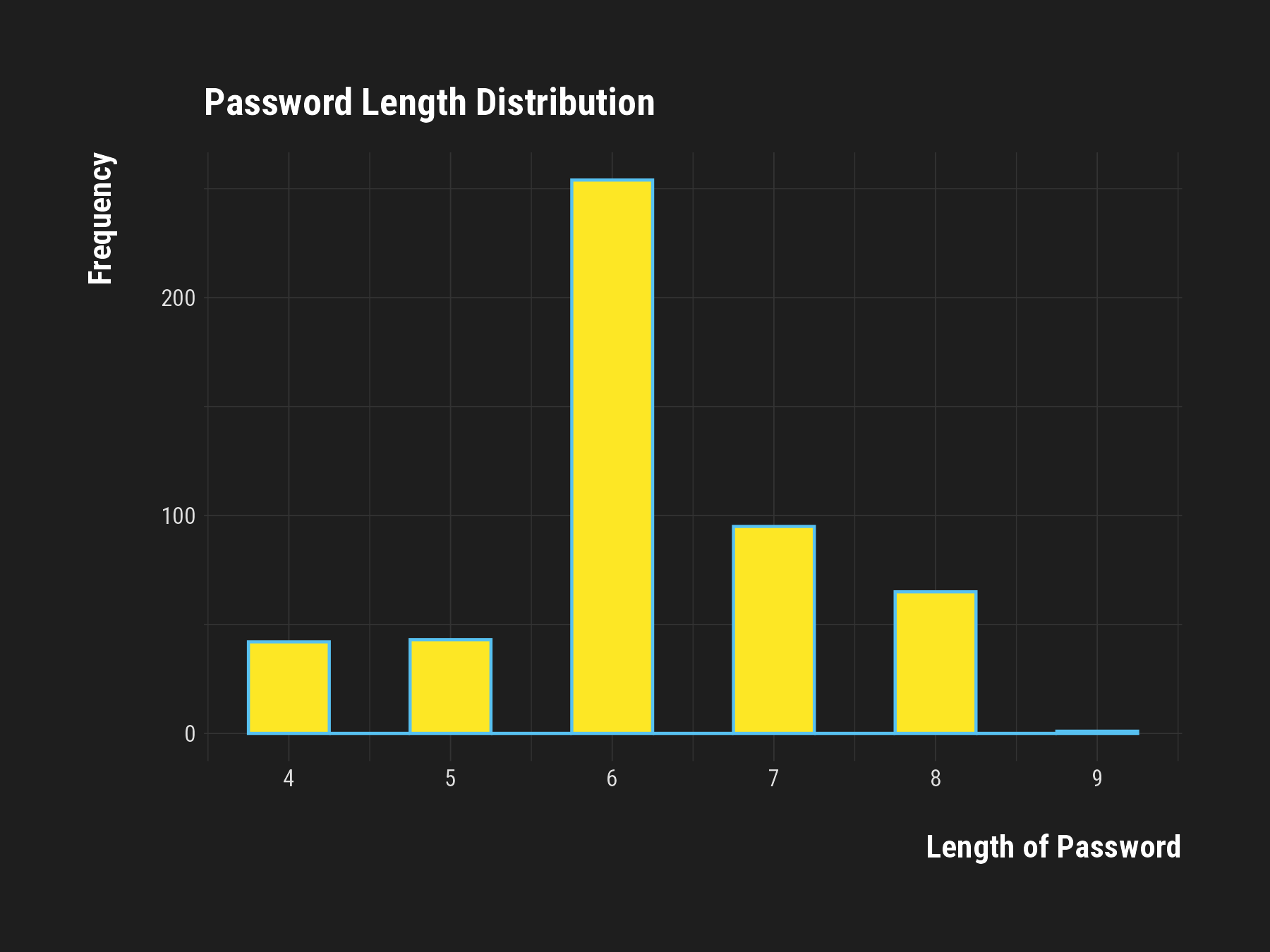
Shortcuts to Breach: Password Length Analysis
- Length Matters: Majority of passwords fall within a risky, short length.
- Six Characters: The most common password length, yet easily crackable.
- Strength in Numbers: Longer passwords are less frequent but more secure.
Dissecting Password Strength by Category
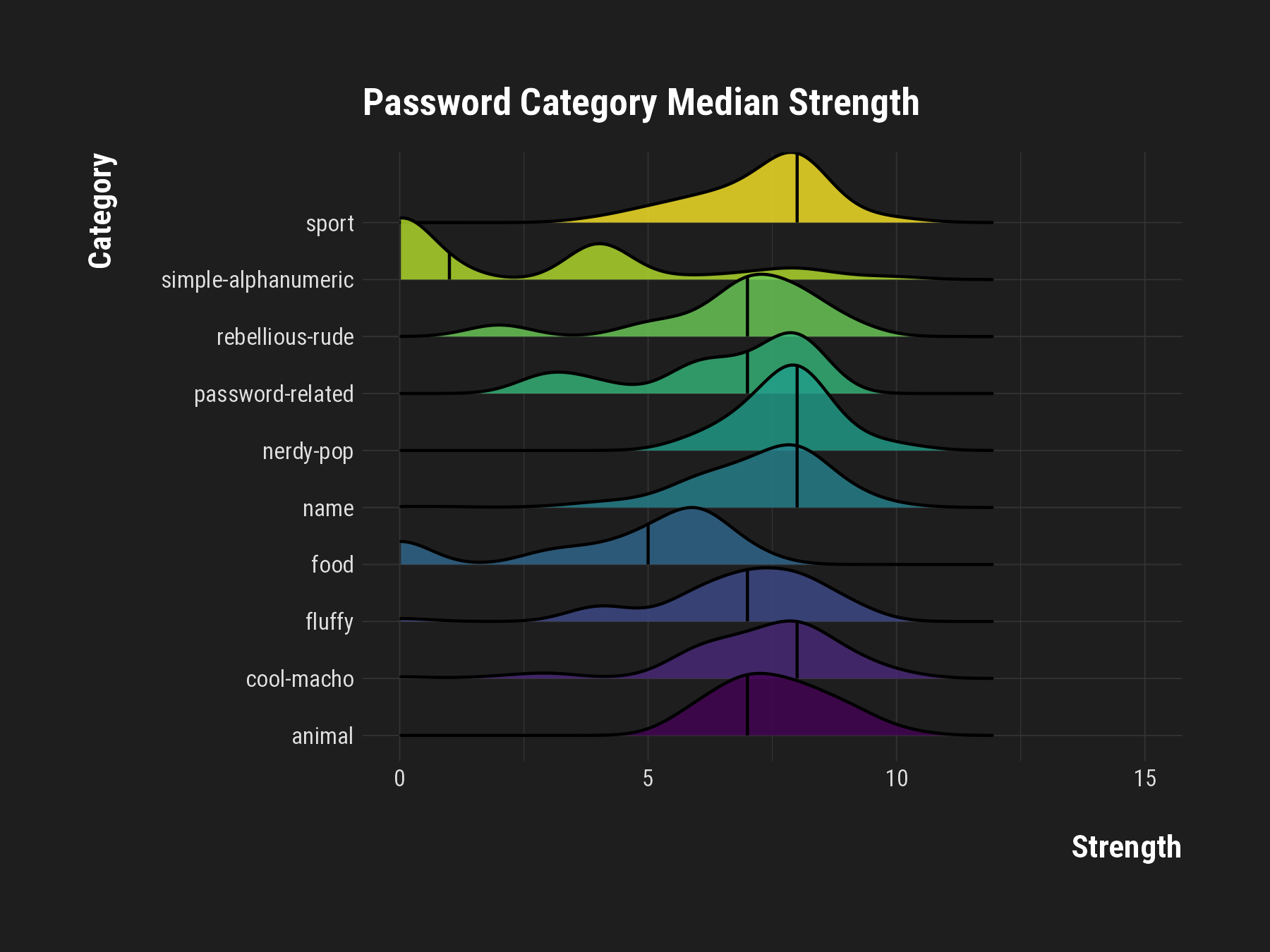 Median Strength Across Categories
Median Strength Across Categories
- Diverse Profiles: Median strength varies, indicating different risk levels.
- Alphanumeric Edge: Categories with alphanumeric combinations show resilience.
- Weak Spots: Common words and patterns are the weakest links.
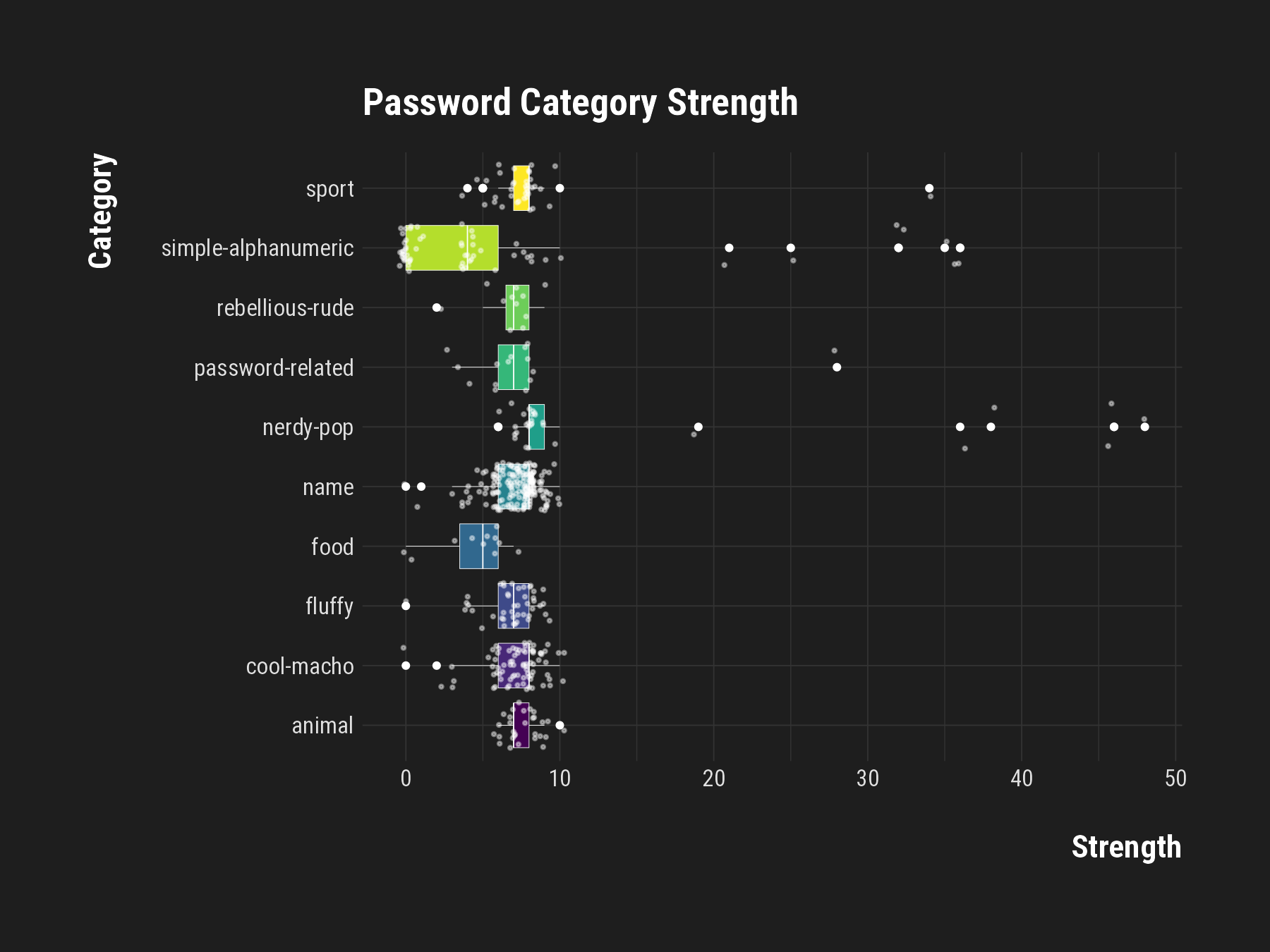 Spread of Password Strength
Spread of Password Strength
- Outliers Exposed: Some passwords show unexpected strength within their categories.
- Consistency in Weakness: Several categories consistently score low on strength.
- A Case for Complexity: Mix of both weak and strong password habits.
Strength by Type and Crack Times
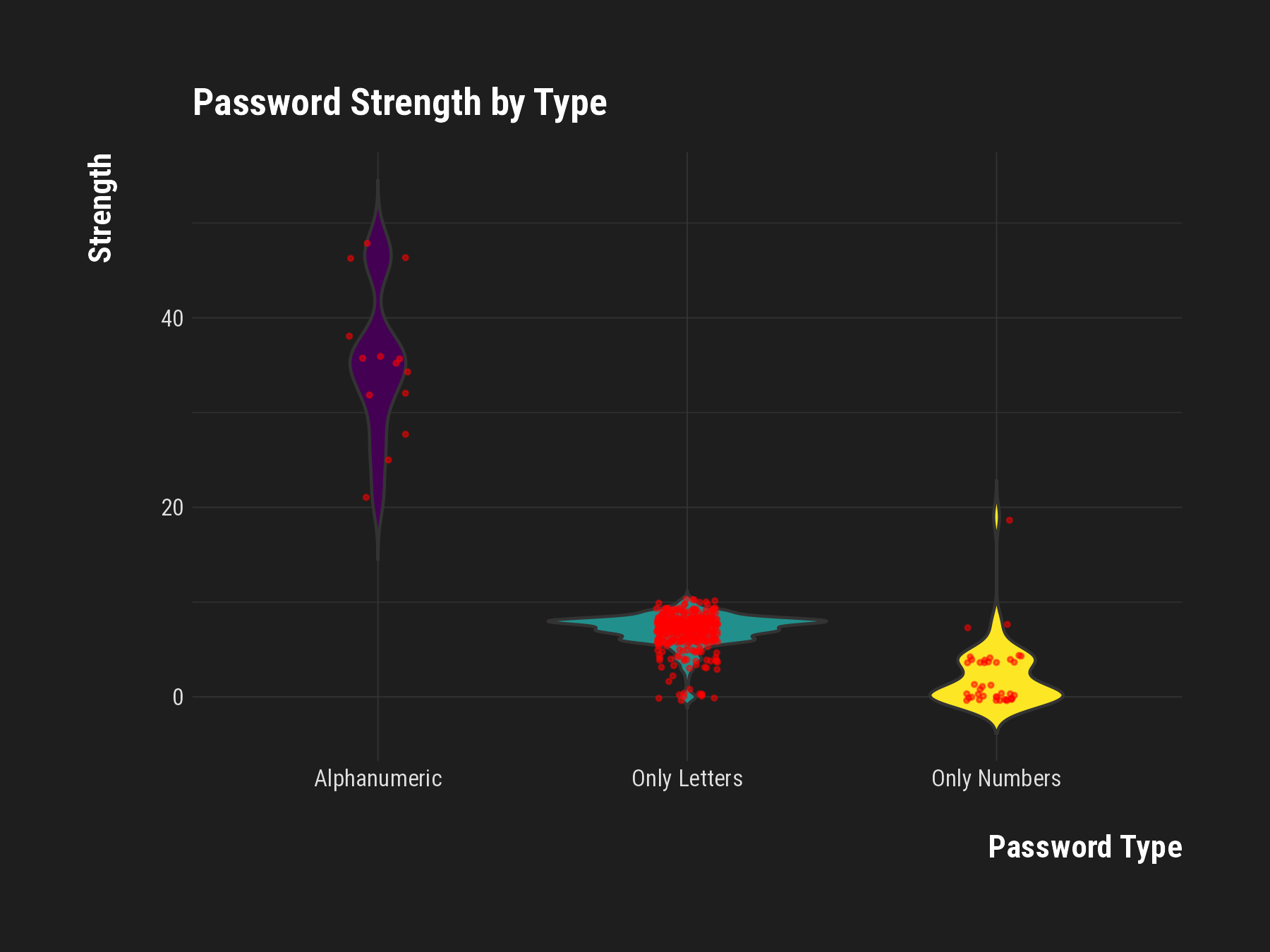 Strength Variations
Strength Variations
- Type Matters: Alphanumeric passwords are stronger than numeric or letter-only types.
- Variability: Alphanumeric passwords vary widely in strength, suggesting diverse complexity.
- Weakness in Simplicity: Single-type passwords are predictably weaker and more vulnerable.
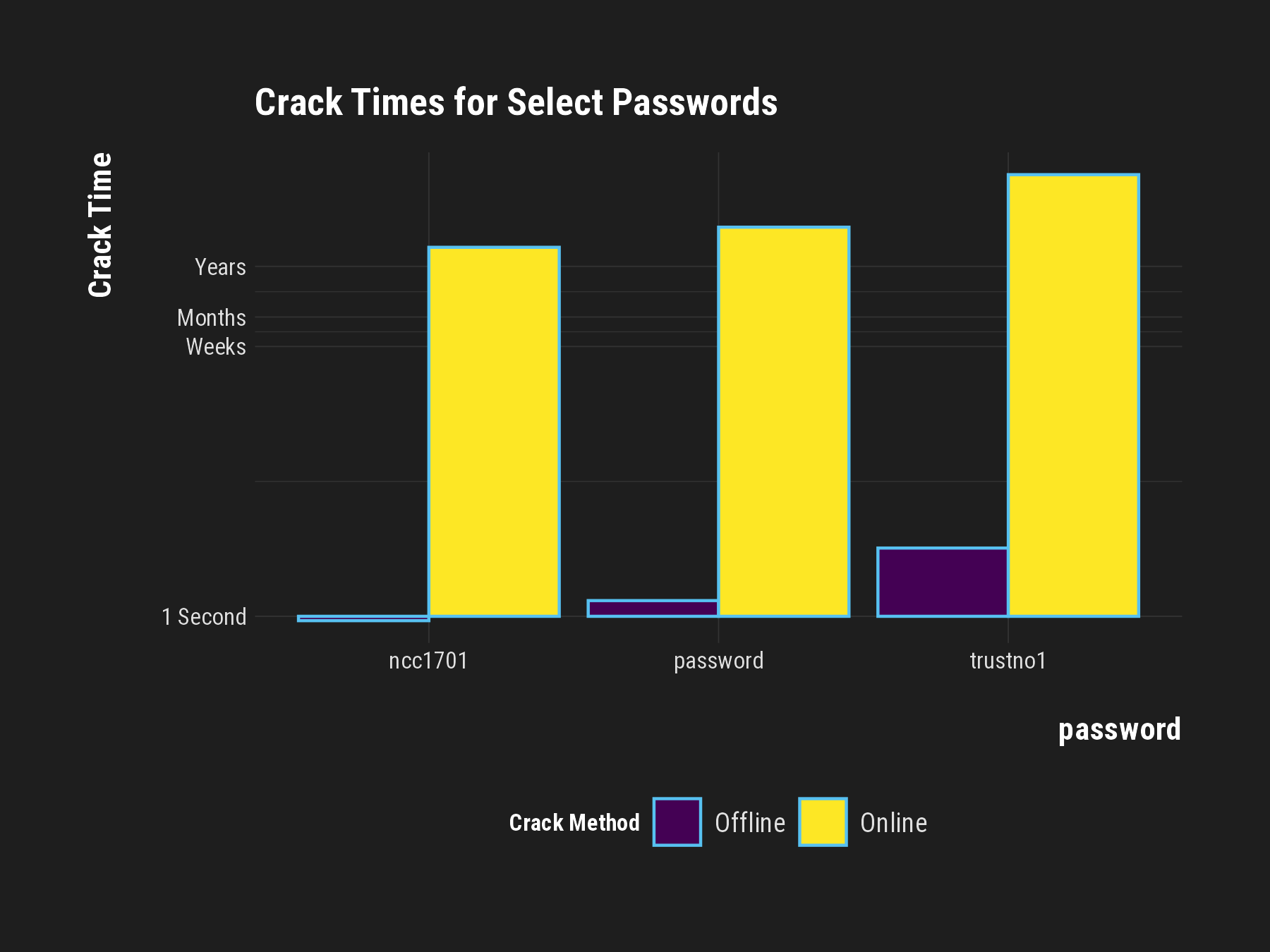 Cracking Timeframes
Cracking Timeframes
- Online vs. Offline: Crack times vary greatly between online and offline attacks.
- Nearly all weak passwords can be cracked within seconds.
- Why does “password” take longer to crack compared to ncc1701?
Online vs Offline Password Cracking
Online Attacks
- Involves guessing login credentials via interfaces for legitimate users (e.g., web pages, SSH servers).
- Methods: Dictionary and Brute Force attacks.
- Slower and noisier, easily detectable via logs.
- Can be mitigated by limiting login attempts and account lockouts.
Offline Attacks
- Cracks passwords from storage files (e.g., SAM or /etc/shadow) after gaining system access.
- Methods: Brute Force, Mask, Dictionary, Rule-Based, and Hybrid attacks.
- Much faster than online cracking; leaves no trace on the target system.
- Mitigated by using strong hashing algorithms with salting and iterations.
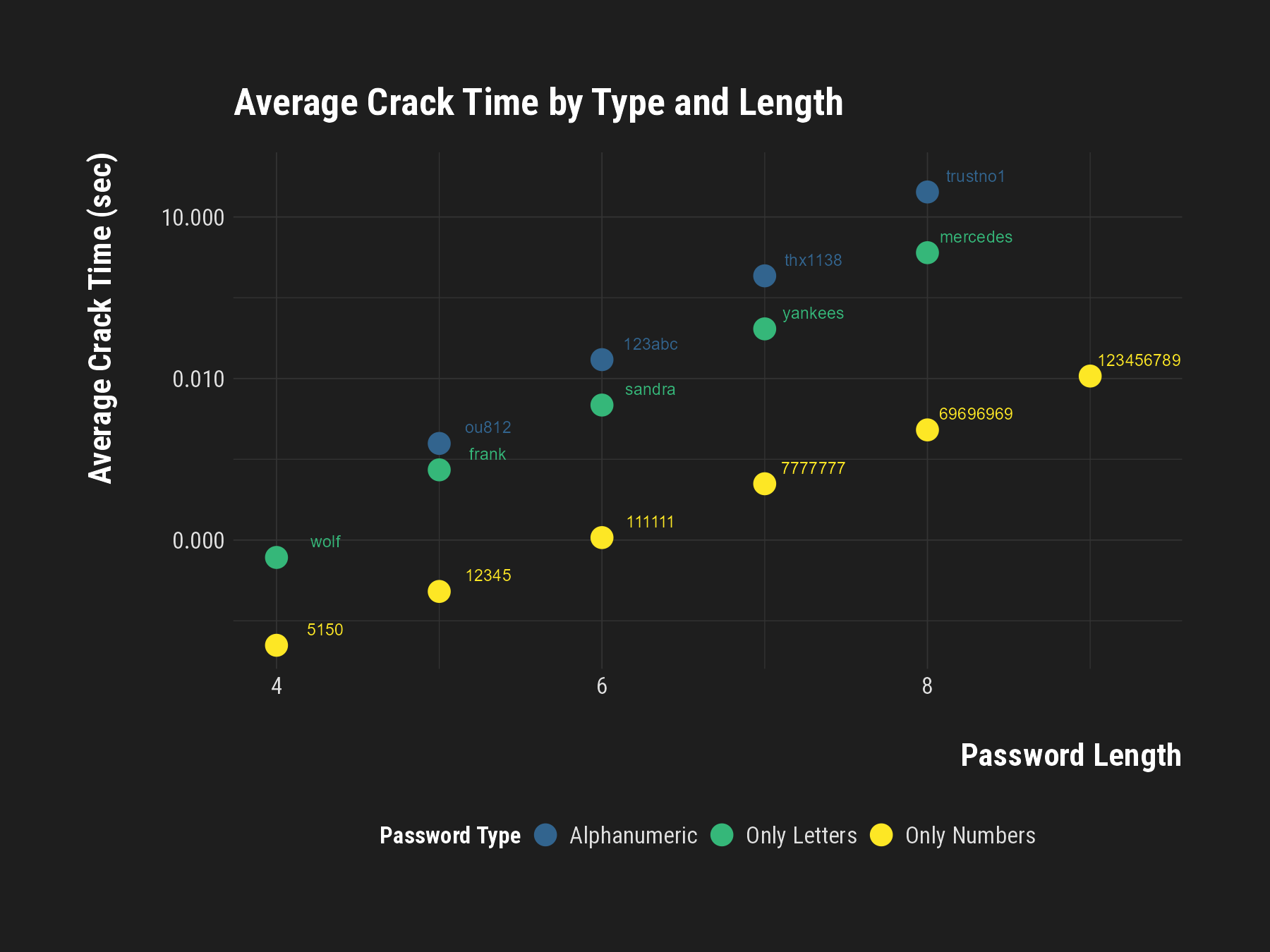
Which is More Important? Type or Length?
Analyzing Crack Time by Password Characteristics
- Length vs. Complexity: Longer passwords aren’t always stronger; complexity also plays a key role.
- Alphanumeric Robustness: Passwords that mix letters and numbers tend to require more time to crack.
- Simple Patterns at Risk: Passwords with simple numeric or alphabetic patterns are cracked much faster, regardless of length.
#thinkrandom
- Length Advantage
- Effective Communication
- Breaking Stereotypes
- Enhanced Usability
Or Does Your Password Matter At All?
- Credential Stuffing: High frequency, low difficulty attacks that rely on user password reuse.
- Phishing: Targets user behavior, not password strength.
- Keystroke Logging: Low frequency but can capture any password regardless of its complexity.
- Local Discovery & Extortion: Relatively rare, these attacks bypass password strength through social engineering or physical access.
- Password Spray & Brute Force: Only effective on common or simple passwords; strong, unique passwords are more resistant.
https://techcommunity.microsoft.com/t5/microsoft-entra-blog/your-pa-word-doesn-t-matter/ba-p/731984
Database Extraction and Cracking, The Scary One
- Database Extraction Threat: Unauthorized retrieval of databases containing sensitive user credentials.
- Hashing: Converts passwords into secure, non-reversible hashes using algorithms like SHA256.
- Salting: Adds unique data to each password before hashing to prevent identical hashes for the same passwords.
- Attack Complexity: More challenging in robust systems like cloud environments due to additional security layers. Easier in on-premises systems if attackers gain high-level access.
**Database full of hashes stolen - how do they proceed?
- Get a cracking rig.
- Do the homework to figure out the algorithm
- Build an initial list of passwords to try.(Billions of passwords disclosed)
- Try every password on that list against the target account.
- Run every allowable password going as far as the rig and time will allow.
Password Cracking Times in 2023


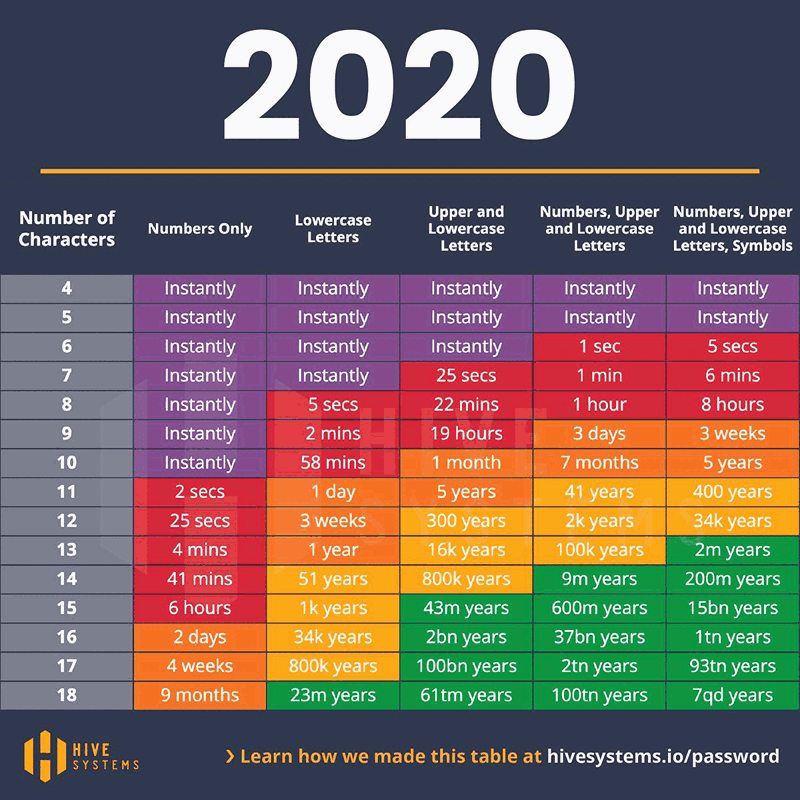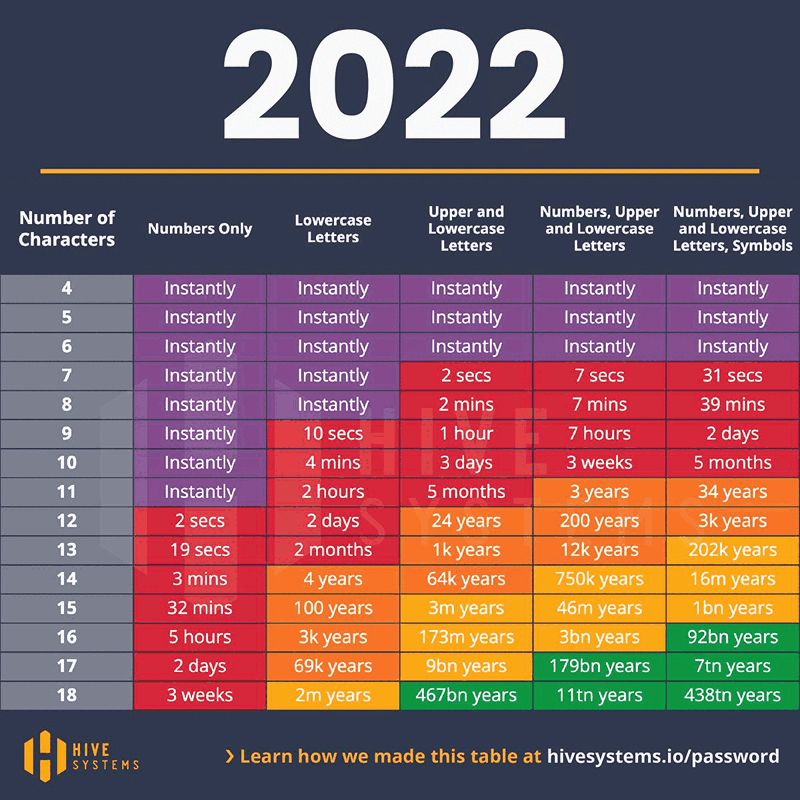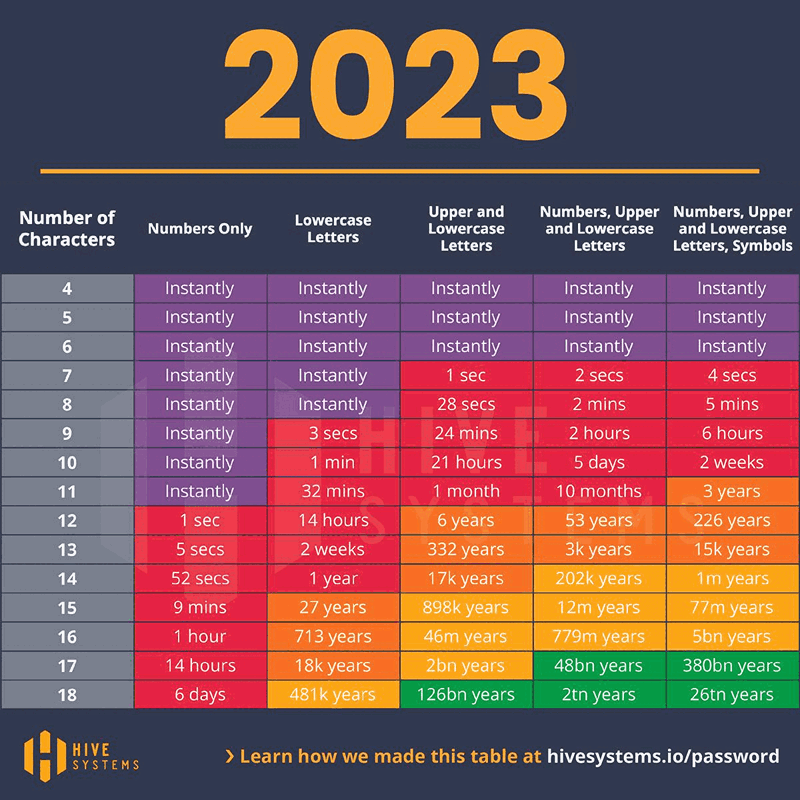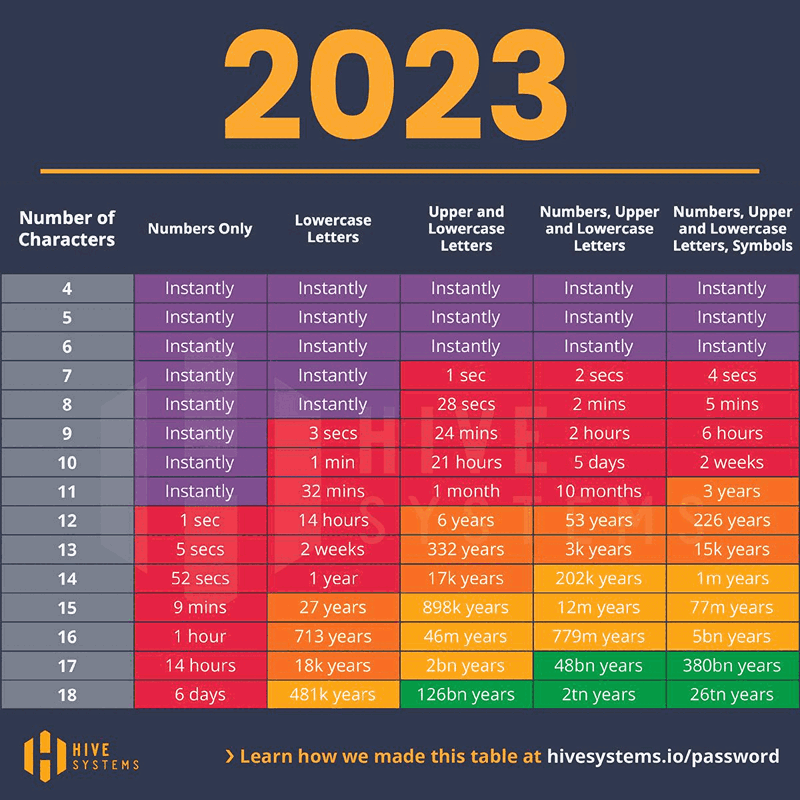
Conclusion
- Password Effectiveness in Breaches: In breaches, password length and uniqueness are crucial. Passwords over 12 characters, ideally generated by password managers, offer better security.
- Password Manager Benefits: Generates long, random strings, enhancing security. Issues include usability and being a high-value target, but they significantly mitigate risks in database breaches.
- MFA as a Crucial Security Layer: Significantly more effective than just password protection. Accounts with MFA are over 99.9% less likely to be compromised.
Key Takeaway: While strong, unique passwords are important, enabling Multi-Factor Authentication (MFA) is a critical step in safeguarding your accounts.